How To Grant Users Rights To Manage Services In Windows 10
By default, common (not-admin) users cannot manage Windows services. This means that users cannot end, start, restart, or alter the settings/permissions of Windows services. In some cases, it is necessary for a user to have the permissions to restart or manage sure services. In this article we'll look at several ways to manage the permissions for Windows services. In particular, we'll show y'all how to let a non-admin user to start, terminate and restart a specific Windows service past granting the appropriate permissions.
Suppose, you need to grant the domain account contoso\tuser the permissions to restart the Print Spooler service (service proper noun – spooler). When the non-admin tries to restart the service, an fault appears:
Organization fault 5 has occurred. Admission is denied.
There is no simple and convenient built-in tool to manage services permissions in Windows. We'll consider some means to grant the permissions to a user to manage service:
Contents:
- Setting Windows Service Permissions Using the SC.exe (Service controller) Tool
- Using the SubInACL to Permit a User to Showtime/Cease/Restart Service
- How to Alter Windows Service Permission Using Procedure Explorer?
- Setting Windows Service Permissions Using PowerShell
- Using Security Templates to Manage Service Permissions
- How to Grant Users Rights to Manage a Service using GPO?
Setting Windows Service Permissions Using the SC.exe (Service controller) Tool
A standard born Windows method to manage arrangement service permissions supposes using the sc.exe (Service Controller) tool. The main trouble with using this utility is the complex syntax of the service permissions format (the SDDL format — Security Description Definition Linguistic communication).
You tin become the electric current permissions for a Windows service as an SDDL string like this:
sc.exe sdshow Spooler
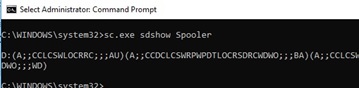
D:(A;;CCLCSWLOCRRC;;;AU)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)
(A;;CCLCSWRPWPDTLOCRRC;;;SY)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)
What do all these symbols mean?
S: — Arrangement Access Control Listing (SACL) D: — Discretionary ACL (DACL)
The first letter afterward brackets means: allow (A) or deny (D).
The next set of symbols is assignable permissions.
CC — SERVICE_QUERY_CONFIG (request service settings) LC — SERVICE_QUERY_STATUS (service status polling) SW — SERVICE_ENUMERATE_DEPENDENTS LO — SERVICE_INTERROGATE CR — SERVICE_USER_DEFINED_CONTROL RC — READ_CONTROL RP — SERVICE_START WP — SERVICE_STOP DT — SERVICE_PAUSE_CONTINUE
The terminal 2 characters are the objects (user, grouping or SID) that are granted permissions. There is a list of predefined groups.
AU Authenticated Users AO Account operators RU Alias to allow previous Windows 2000 AN Anonymous logon AU Authenticated users BA Built-in administrators BG Built-in guests BO Backup operators BU Built-in users CA Certificate server administrators CG Creator group CO Creator possessor DA Domain administrators DC Domain computers DD Domain controllers DG Domain guests DU Domain users EA Enterprise administrators ED Enterprise domain controllers WD Everyone PA Group Policy administrators IU Interactively logged-on user LA Local ambassador LG Local invitee LS Local service account SY Local system NU Network logon user NO Network configuration operators NS Network service business relationship PO Printer operators PS Personal self PU Power users RS RAS servers group RD Terminal server users RE Replicator RC Restricted code SA Schema administrators SO Server operators SU Service logon user
Instead of a predefined group, you can explicitly specify a user or group by SID. To get the SID for the current user, you can use the command:
whoami /user
Or you tin can find the SID for whatsoever domain user using the Get-ADUser cmdlet:
Become-ADUser -Identity 'sadams' | select SID
You lot can become the SID of the Advertizing security group using the Get-ADGroup cmdlet:
Get-ADGroup -Filter {Name -eq "ny-ithelpdesk"} | Select SID
In order to assign the SDDL permissions string for a specific service, you can use the sc sdset command. For example, the permissions can be granted to a user with the following command:
sc sdset Spooler "D:(A;;CCLCSWRPWPDTLOCRRC;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;CCLCSWLOCRRC;;;SU)(A;;RPWPCR;;;S-ane-five-21-2133228432-2794320136-1823075350-one thousand)Southward:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)"
Using the SubInACL to Allow a User to Start/Finish/Restart Service
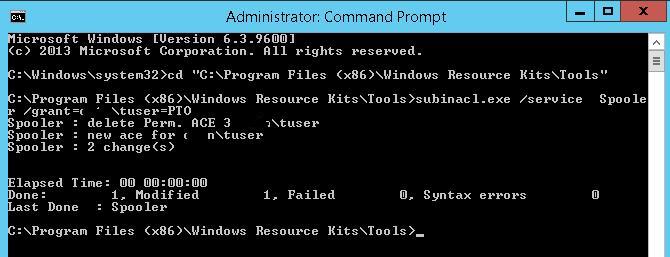
Information technology is easier to employ a command line tool SubInACL from the Sysinternals (by Mark Russinovich) to manage the service permissions. The syntax of this tool is much easier and more convenient. Hither is how you can grant the restart permissions for a service using the SubInACL:
- Download subinacl.msi from this webpage (https://www.microsoft.com/en-united states of america/download/details.aspx?id=23510) and install it on the target organisation;
- In the elevated command prompt, go to the directory containing the tool:
cd "C:\Program Files (x86)\Windows Resource Kits\Tools\" - Run the command:
subinacl.exe /service Spooler /grant=contoso\tuser=PTO
If you need to grant permissions to a service running on a remote estimator, employ the following syntax of the subinacl command:Note. In this case we take granted a user the permissions to suspend (interruption/continue), start and cease (restart) a service. The total listing of the available service permissions:
F : Total Control R : Generic Read Due west : Generic Write X : Generic eXecute L : Read controL Q : Query Service Configuration Due south : Query Service Condition E : Enumerate Dependent Services C : Service Change Configuration T : Beginning Service O : Stop Service P : Pause/Go on Service I : Interrogate Service U : Service User-Defined Control Commands
subinacl /SERVICE \\lon-prnt1\spooler /grant=contoso\tuser=F - At present you only accept to logon the computer under a user business relationship and try to restart the service with the commands:
internet end spooler
net starting time spooler
or
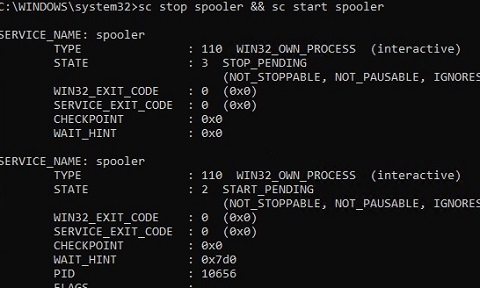
sc stop spooler && sc start spooler
If yous did everything right, the service should restart.
To revoke the assigned service permissions, use the /revokepick of the subinacl.exe tool. For instance:
subinacl.exe /service Spooler /revoke=contoso\tuser
How to Alter Windows Service Permission Using Process Explorer?
You can alter Windows service permissions using 1 more Sysinternals utility – Process Explorer. Run the Procedure Explorer every bit administrator and find the process of the service y'all need. In our example, this is spoolsv.exe (the spooler executable – C:\Windows\System32\spoolsv.exe). Open the process backdrop and click the Services tab.
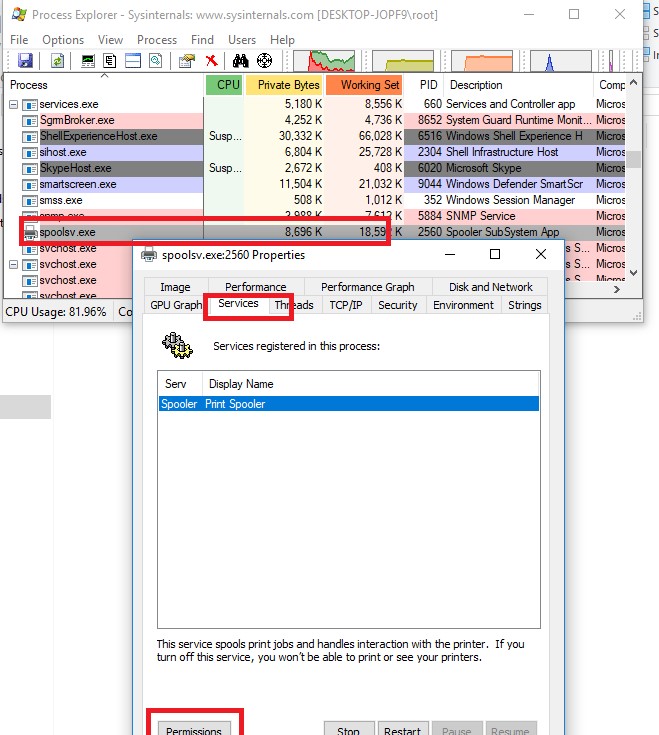
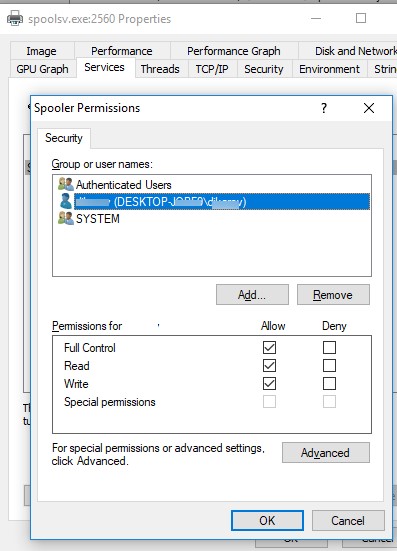
Click the Permissions push and add the user or group in the window that opens. After that select the permissions that you lot want to assign (Full Command/Write/Read).
Setting Windows Service Permissions Using PowerShell
In TechNet gallery there is a dissever unofficial PowerShell module for managing permissions for different Windows objects – PowerShellAccessControl Module (you tin download it hither). This module too allows you lot to manage the service permissions. Install this module and import it into your PS session:
Import-Module PowerShellAccessControl
You can get the constructive permissions for a specific Windows service from PowerShell like this:
Get-Service spooler | Become-EffectiveAccess -Principal corp\tuser
To allow not-admin user to start and stop spooler service, run the command:
Become-Service spooler | Add-AccessControlEntry -ServiceAccessRights Kickoff,Stop -Principal corp\tuser
Using Security Templates to Manage Service Permissions
A visual (but requiring more actions) graphical way to manage service permissions is using Security Templates. Open up mmc.exe console and add the Security Templates snap-in.
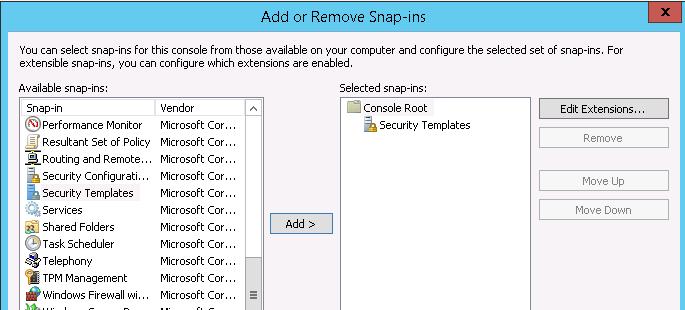
Create a new security template (New Template).
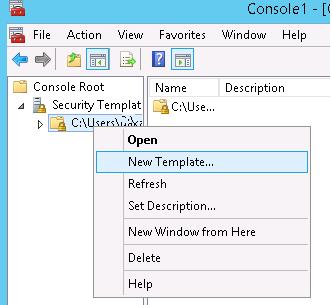
Specify the proper name for the new template and go to the Organization Services section. In the list of services select the service Print Spooler and open its properties.
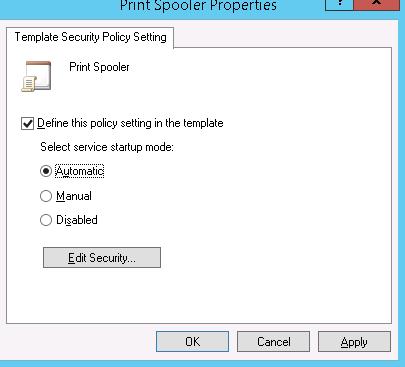
Select the startup mode (Automated) and click Edit Security.
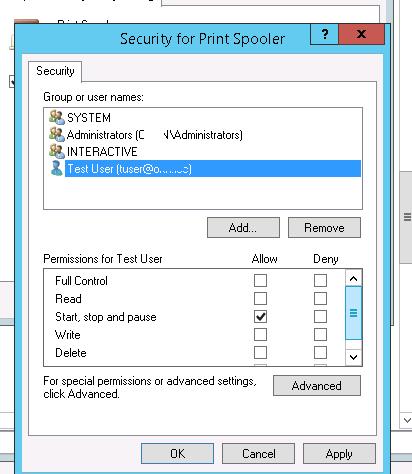
Using the Add push button, add together a user account or a group to grant permissions to. In our case, Start, finish and pause permission is plenty.
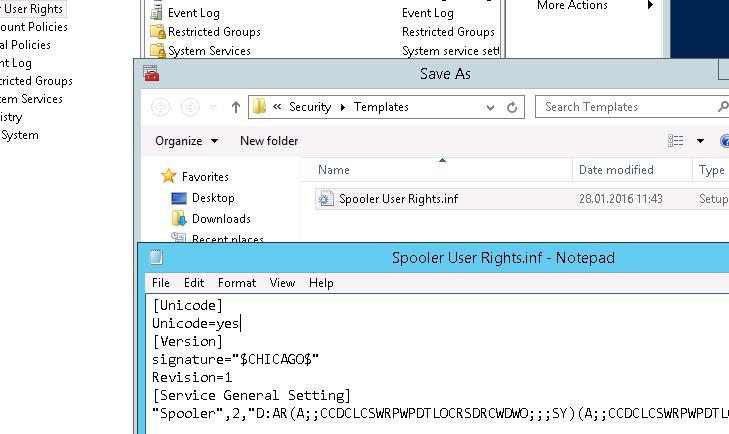
Relieve this template.
Note. The content of the Security Template is saved as the INF file in the C:\Users\%username%\Documents\Security\Templates folder.
If you open this file, you can run across that the data well-nigh the permissions is saved in the SDDL format, mentioned earlier. The string obtained in this way can be used as an argument of the sc.exe command.
[Unicode]
Unicode=yes
[Version]
signature="$CHICAGO$"
Revision=ane
[Service General Setting]
"Spooler",2,"D:AR(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;SY)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;BA)(A;;CCLCSWLOCRRC;;;IU)(A;;RPWPDTRC;;;South-1-5-21-3243688314-1354026805-3292651841-1127)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD)"
Now you merely have to create a new database (Open Database) using the Security Configuration and Analysis snap-in and import your Security Template from the file Spooler User Rights.inf.
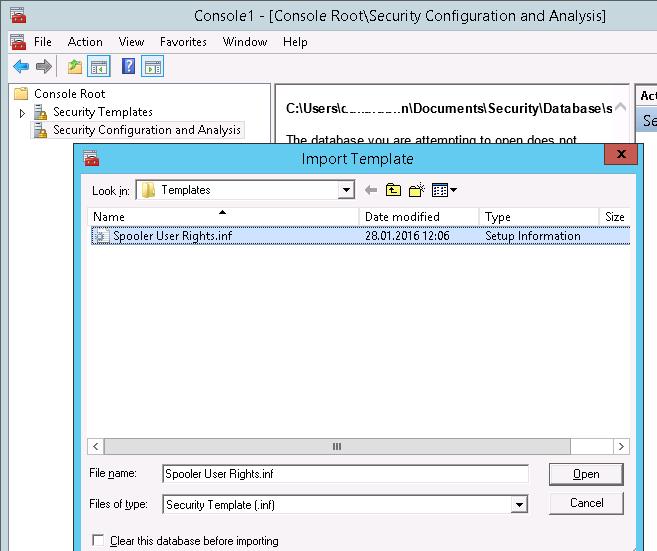
Employ this template by selecting Configure Computer At present pick from the context carte.
At present you lot check that the user tin allow manage the Print Spooler service nether not-admin account.
How to Grant Users Rights to Manage a Service using GPO?
If you accept to grant permissions to users to starting time/stop a service multiple servers or domain reckoner, it's easier to employ Group Policy (GPO) features:
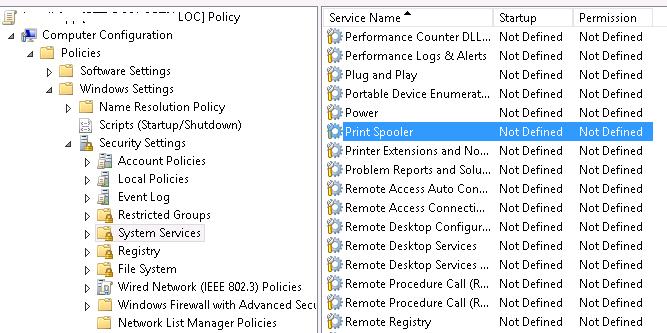
- Create a new GPO or edit the existing one, link information technology to the necessary Active Directory container (OU) with the calculator objects . Go to the policy section Computer configuration -> Windows Settings -> Security Settings -> System Services;
- Detect the Spooler service and grant permissions to the users similar in the method described above. Salve the changes;
- Wait until the GPO is applied on client computers and make certain that the new service permissions have been assigned.
Where are the Windows service security permissions stored?
The security settings for all services for which you changed the default permissions are stored in their own registry key HKLM\System\CurrentControlSet\Services\<servicename>\Security in the Security parameter of the REG_BINARY type.
This means that one of the ways to fix service permissions on other computers is to export/import this registry parameter (including through a GPO).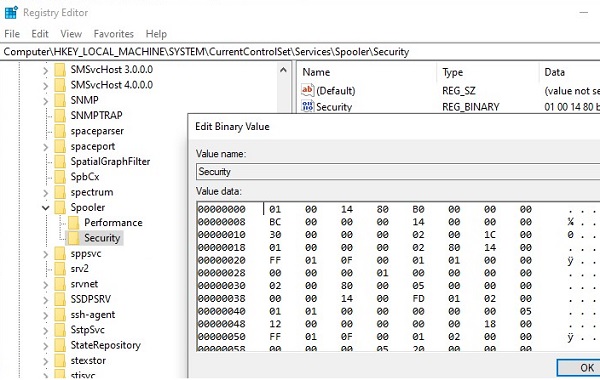
And then, nosotros looked at several ways to manage the Windows service permissions, which allow you to grant any permissions for system services to not-admin user. If the user requires remote access to the service, without granting it local logon or RDP access permissions, you lot must let the user to connect remotely and enumerate services via Service Control Manager.
Source: http://woshub.com/set-permissions-on-windows-service/
Posted by: farrelladlyinit.blogspot.com



0 Response to "How To Grant Users Rights To Manage Services In Windows 10"
Post a Comment